GitLab Vulnerability Report Integration
With StackHawk’s code scanning integration in Gitlab, teams can now run Dynamic API and Application Security Testing (DAST) whenever they check-in code and view results directly in GitLab.
Requirements
StackHawk:
- You must have a StackHawk account.
GitLab:
- You must have login permissions to the GitLab account you wish to add the integration to.
- You must have a GitLab Ultimate plan to access GitLab Security And Compliance Dashboard
- You must have configured StackHawk scanning for your project with GitLab Pipelines
Enabling Vulnerability Reporting in GitLab with HawkScan
This integration can be broken down into four major steps:
- Configuring StackHawk to run in your GitLab pipeline
- Updating your GitLab pipeline to create a DAST report
- Running your pipeline
- Viewing and triaging results
Configuring StackHawk in the GitLab Pipeline
You can add StackHawk scanning to your GitLab pipeline by adding scanning to your .gitlab-ci.yml and adding a stackhawk.yml configuration file to your repository.
Detailed set up instructions can be found in HawkScan and GitLab
Updating GitLab Pipeline to Create a DAST report
Once you have set up scanning in your GitLab pipline, you need to add two things to your .gitlab-ci.yml
First pass in the DAST_ARTIFACT environment variable to tell HawkScan to create a DAST report.
Your updated pipeline report will now look like this:
.gitlab-ci.yml
image: docker
services:
- docker:dind
before_script:
- docker pull stackhawk/hawkscan
hawkscan:
script:
- |
docker run -v $(pwd):/hawk:rw -t \
-e API_KEY="hawk.${HAWK_API_ID}.${HAWK_API_SECRET}" \
-e NO_COLOR=true \
-e DAST_ARTIFACT=1 \
stackhawk/hawkscan
Next add the stackhawk-dast-report.json value to your DAST report artifacts.
.gitlab-ci.yml
artifacts:
reports:
dast: stackhawk-dast-report.json
Your updated StackHawk job should look somethng like this:
.gitlab-ci.yml
image: docker
services:
- docker:dind
before_script:
- docker pull stackhawk/hawkscan
hawkscan:
script:
- |
docker run -v $(pwd):/hawk:rw -t \
-e API_KEY="hawk.${HAWK_API_ID}.${HAWK_API_SECRET}" \
-e NO_COLOR=true \
-e DAST_ARTIFACT=1 \
stackhawk/hawkscan
artifacts:
reports:
dast: stackhawk-dast-report.json
Running Your Pipeline
The actions that trigger your build pipline, such as code changes and creating pull requests, will now trigger running HawkScan and creating a vulnerability report.
Viewing and Triaging Scan Results
The vulnerability report is included in the Security and Complaince section of GitLab.
Vulnerability Report
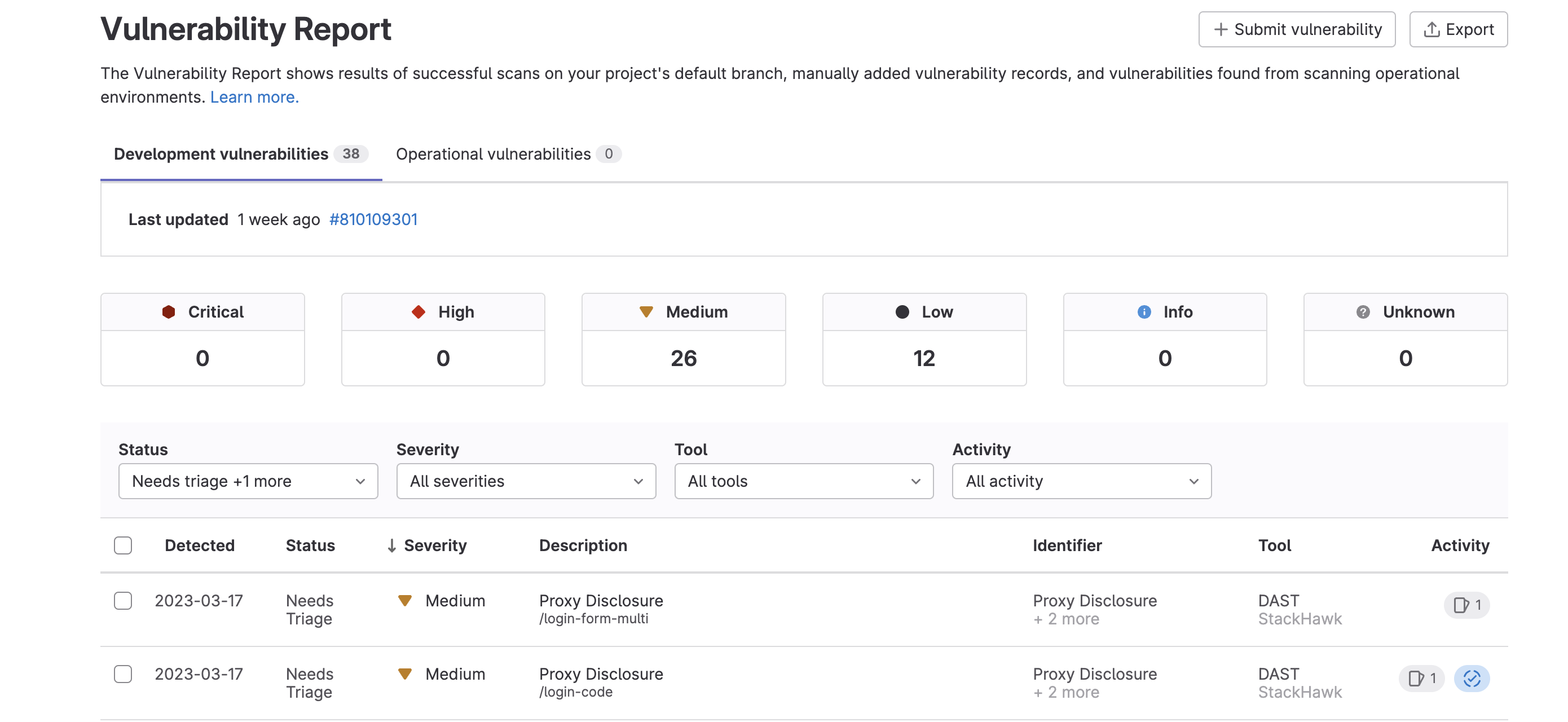
To view the vulnerabilities that StackHawk found in your application, navigate to the Vulnerability Report section of the Security and Compliance center.
 |
This should give you an overview of all your vulnerablities.
 |
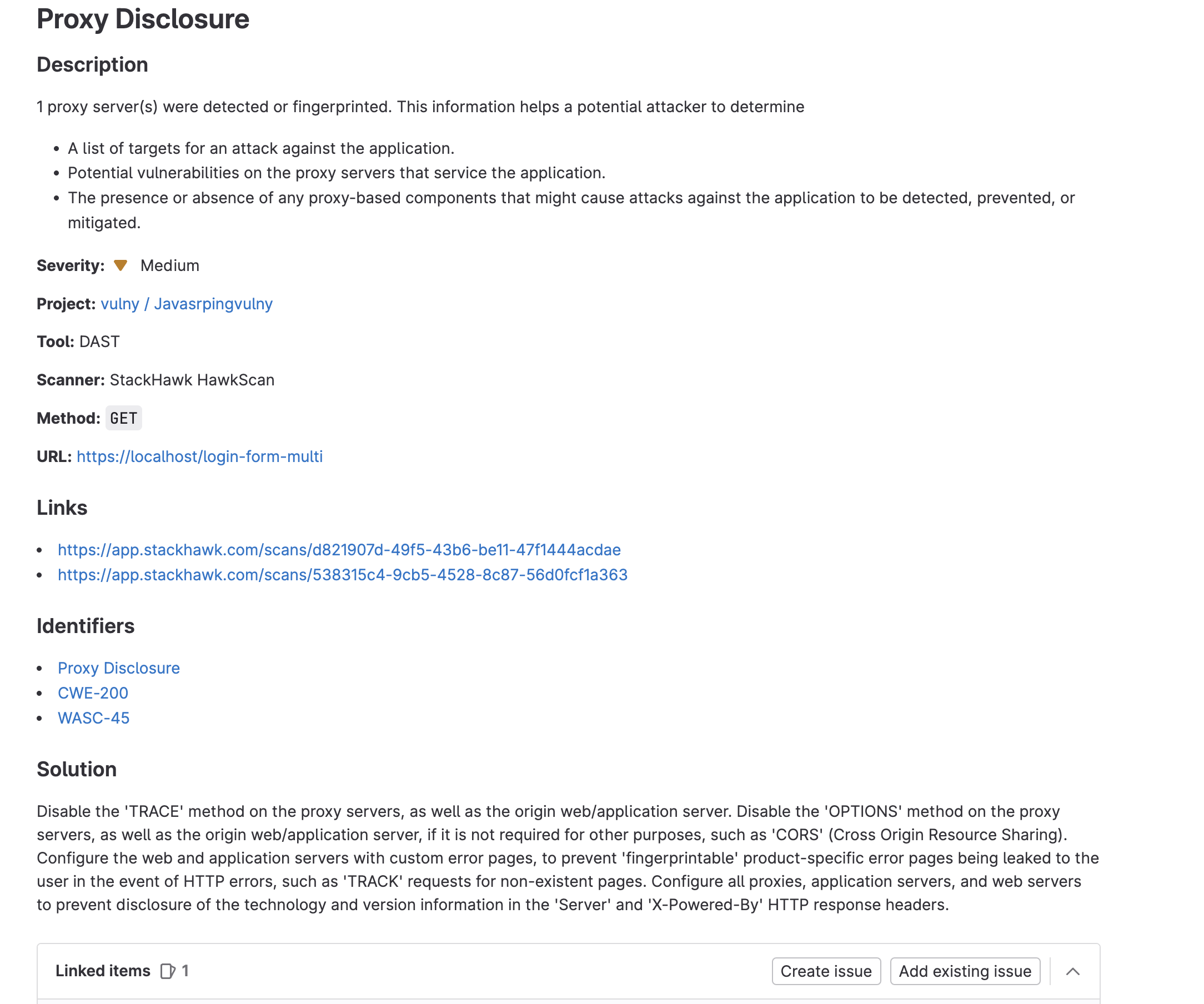
Triaging Vulnerabilities
Click into each vulnerability to view details and create issues by clicking on the Create Issue button on the bottom of the page.
 |

