Integrating StackHawk with Microsoft Defender for Cloud
Overview
StackHawk’s integration with Microsoft Defender for Cloud can be enabled through SARIF (Static Analysis Results Interchange Format), providing detailed security insights directly within your GitHub or Azure DevOps workflows. Here are the two primary ways to set up this integration:
GitHub Action
Configure a GitHub Action to generate SARIF output from StackHawk scans and automatically import the results into Microsoft Defender for Cloud.
To integrate StackHawk with GitHub Actions for SARIF output:
- Ensure you have your StackHawk API Key and a configured stackhawk.yml in your GitHub repository.
- In your repository’s
/settings/secrets/actionspage, set your StackHawk API Key asHAWK_API_KEY. - Add the StackHawk HawkScan Action to your GitHub Actions workflow with the following setup:
# Make sure your app.host web application is started and accessible before you scan.
# - name: Start Web Application
# run: docker run --rm --detach --publish 8080:80 --name my_web_app nginx
- name: API Scan with StackHawk
uses: stackhawk/hawkscan-action@v2.1.3
with:
apiKey: $
env:
SARIF_ARTIFACT: true
Ensure the app.host in stackhawk.yml is accessible. Include with.env.SARIF_ARTIFACT: true for SARIF output. For more configurations, refer to the HawkScan Action documentation.
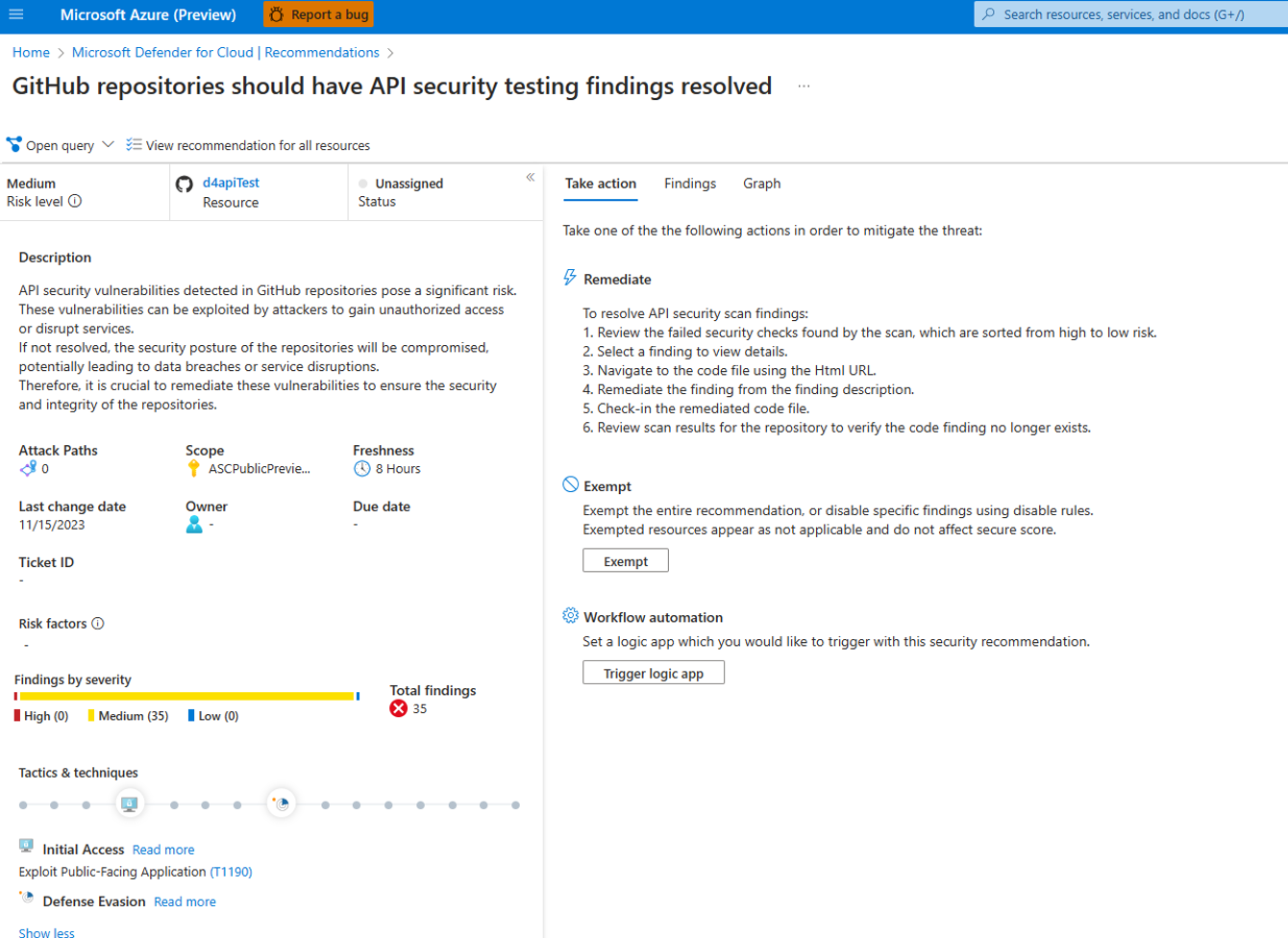
To access API security testing recommendations in Defender for Cloud:
Navigate to the Defender for Cloud dashboard.
- Click on “Recommendations”.
- Use the search bar to filter for “API security testing”.
- Locate and select the recommendation that reads: “GitHub repositories should have API security testing findings resolved.”
Azure DevOps
Use Azure DevOps to run StackHawk scans that produce SARIF output, facilitating seamless integration with Microsoft Defender for Cloud.
To set up the StackHawk HawkScan Extension in Azure DevOps Pipelines:
- Ensure you are logged into Azure DevOps Pipelines and have a StackHawk account.
- Use an existing azure-pipelines.yml or create a new pipeline to scan your GitHub repository for API vulnerabilities.
- Install the HawkScan Extension in your Azure DevOps Organization, and configure your pipeline with the HawkScanInstall and RunHawkScan tasks as follows:
- task: HawkScanInstall@1.2.8
inputs:
version: "3.7.0"
installerType: "msi"
# start your web application in the background
# - script: |
# curl -Ls https://GitHub.com/kaakaww/javaspringvulny/releases/download/0.2.0/java-spring-vuly-0.2.0.jar -o ./java-spring-vuly-0.2.0.jar
# java -jar ./java-spring-vuly-0.2.0.jar &
- task: RunHawkScan@1.2.8
inputs:
configFile: "stackhawk.yml"
version: "3.7.0"
env:
HAWK_API_KEY: $(HAWK_API_KEY) # use variables in the azure devops ui to configure secrets and env vars
APP_ENV: $(imageName)
APP_ID: $(appId)
SARIF_ARTIFACT: true
Include the SARIF_ARTIFACT: true in the environment settings of the RunHawkScan task to enable SARIF output. This setup targets the app.host defined in your stackhawk.yml.
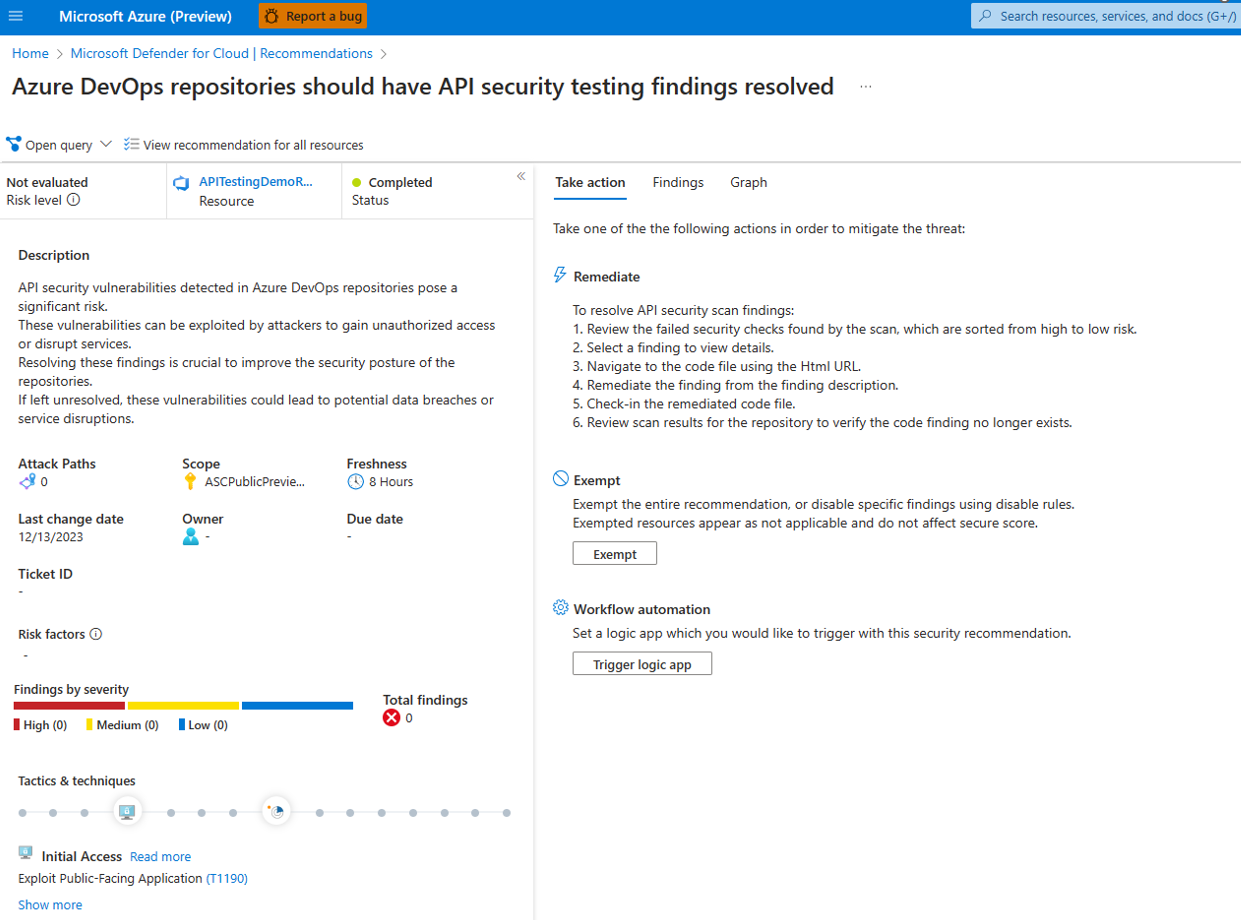
Navigate to the Defender for Cloud dashboard.
- Click on “Recommendations”.
- Use the search bar to filter for “API security testing”.
- Locate and select the recommendation that reads: “Azure DevOps repositories should have API security testing findings resolved”
Feedback
Have any suggestions, feature requests, or feedback to share? Contact StackHawk Support .

