API Discovery
This feature is available on the StackHawk Enterprise plan.
StackHawk’s API Discovery feature automatically identifies all of your organization’s APIs, microservices, and web applications from connected code repositories. By leveraging advanced AI to analyze your source code repositories, StackHawk can give a real-time overview of your API Attack Surface. AI-driven insights and thoughtful prioritization will help you focus on the services that need immediate coverage while seamlessly integrating API and Application testing into your DevOps workflows. By relying on your codebase as the single source of truth, StackHawk ensures you catch every application and API before vulnerabilities reach production.
Why Use API Discovery?
- Identify Hidden Endpoints
Modern applications often consist of numerous microservices and external integrations. Without continuous discovery, unknown or shadow APIs can slip through the cracks and remain untested. API Discovery ensures every endpoint is accounted for. - Strengthen Your Security Posture
By surfacing your API Attack Surface directly from the source code, teams gain immediate visibility into potential entry points. This allows you to shift security left, fixing vulnerabilities early in the development lifecycle. - Save Time & Resources
Manual audits can be time-consuming and error-prone. Automated API Discovery helps teams avoid repetitive, manual searches for new services or code changes—freeing up developers and security engineers to focus on higher-value work. - Integrate Seamlessly with DevOps
The process is frictionless for Security teams. Because StackHawk plugs directly into your source code repo, you’ll always have an up-to-date inventory of your attack surface without additional maintenance or configuration.
How It Works
- Connect Your Repositories
StackHawk integrates with major SCM platforms (GitHub, GitLab, Azure Repos, Bitbucket) to securely retrieve repository details and enable automatic discovery. - AI-Driven Analysis
Advanced AI examines your code structures and metadata to pinpoint testable applications and APIs, giving you a clear understanding of your evolving API Attack Surface. - Real-Time Visibility & Prioritization
Discovered services appear in your API Discovery view, where you can instantly gauge which ones need immediate coverage. With strategic recommendations, it’s easy to integrate testing into your DevOps workflow. - Continuous Updates
When repositories change or new ones emerge, StackHawk automatically surfaces them—ensuring you never miss critical APIs or services that need security attention.
Feature Overview
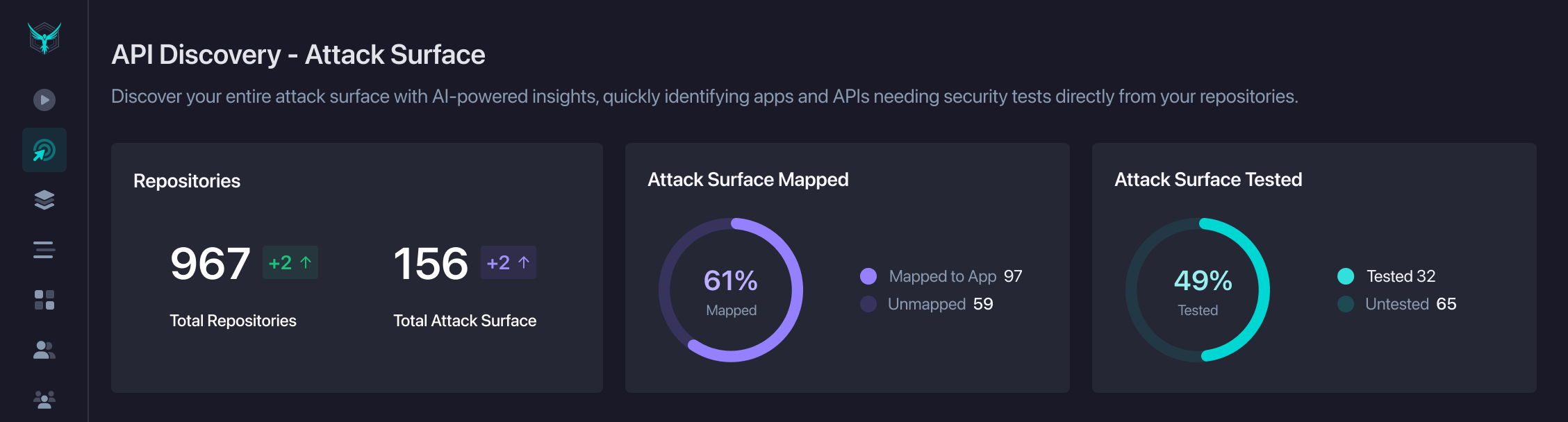
The first step in getting your APIs and applications secured with StackHawk is knowing what you have covered and what still needs to be tested.
The Attack Surface Coverage view shows two key things:
- Mapped – Repositories linked to a StackHawk application, either by connecting to an existing app or creating one from the repo. This is the first step toward testing.
- Tested - Mapped repositories that have had at least one scan run.
Use this to quickly spot gaps, focus on untested mapped repos, and track progress toward full coverage.
Attack Surface Repositories
Shows all of the repositories that are part of your Attack Surface, either discovered using HawkAI or manually added. Here you have the ability to connect these repositories to new or existing Applications so that you can get them tested with StackHawk. In this view you can see the name of the repository, its status within StackHawk, the frameworks detected by HawkAI, last commit information and recent commit activity. From the menu (…) on each row you are able to remove the repository from the Attack Surface or manage which Applications it is connected to.
For repositories that HawkAI has identified as an API or Web Application, you’ll notice the star icon next to its name indicating it has been automatically added to your attack surface. You can easily remove a repository from the attack surface if it isn’t something you plan to cover with StackHawk.
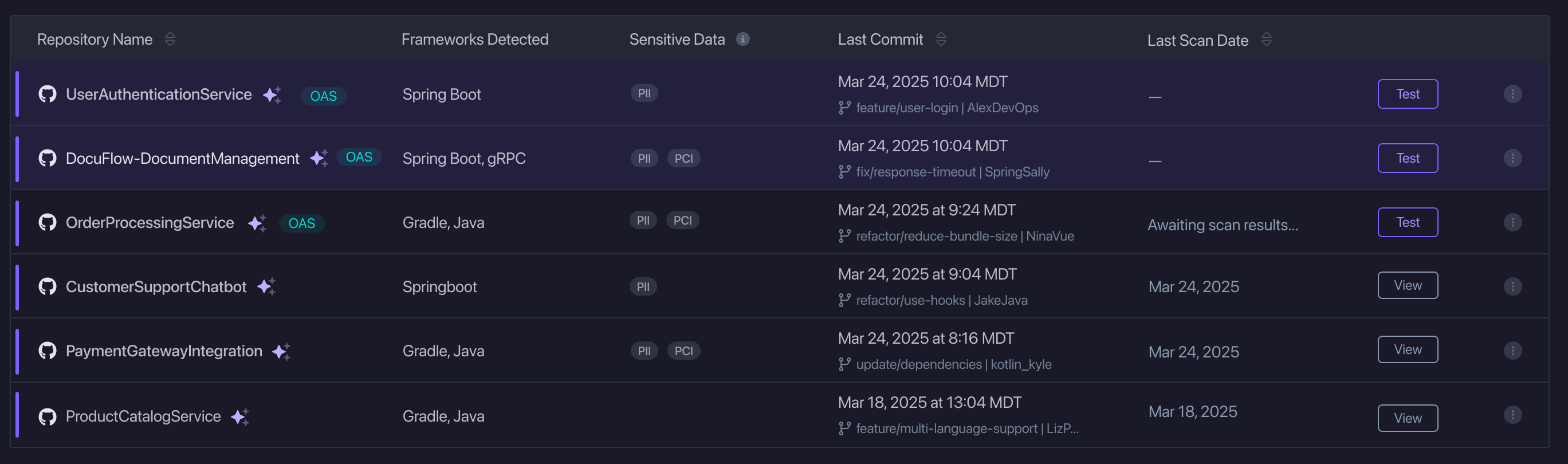
The number of StackHawk Applications a repository is mapped to is displayed in the StackHawk Applications column. There is no limit to the number of applications that can be mapped to a repository. The benefit of mapping repositories to applications is that all scans will always be associated with that specific code. This way, you can maintain continuous visibility over the code written within your organization and the security tests you run to ensure complete coverage of your applications and APIs.
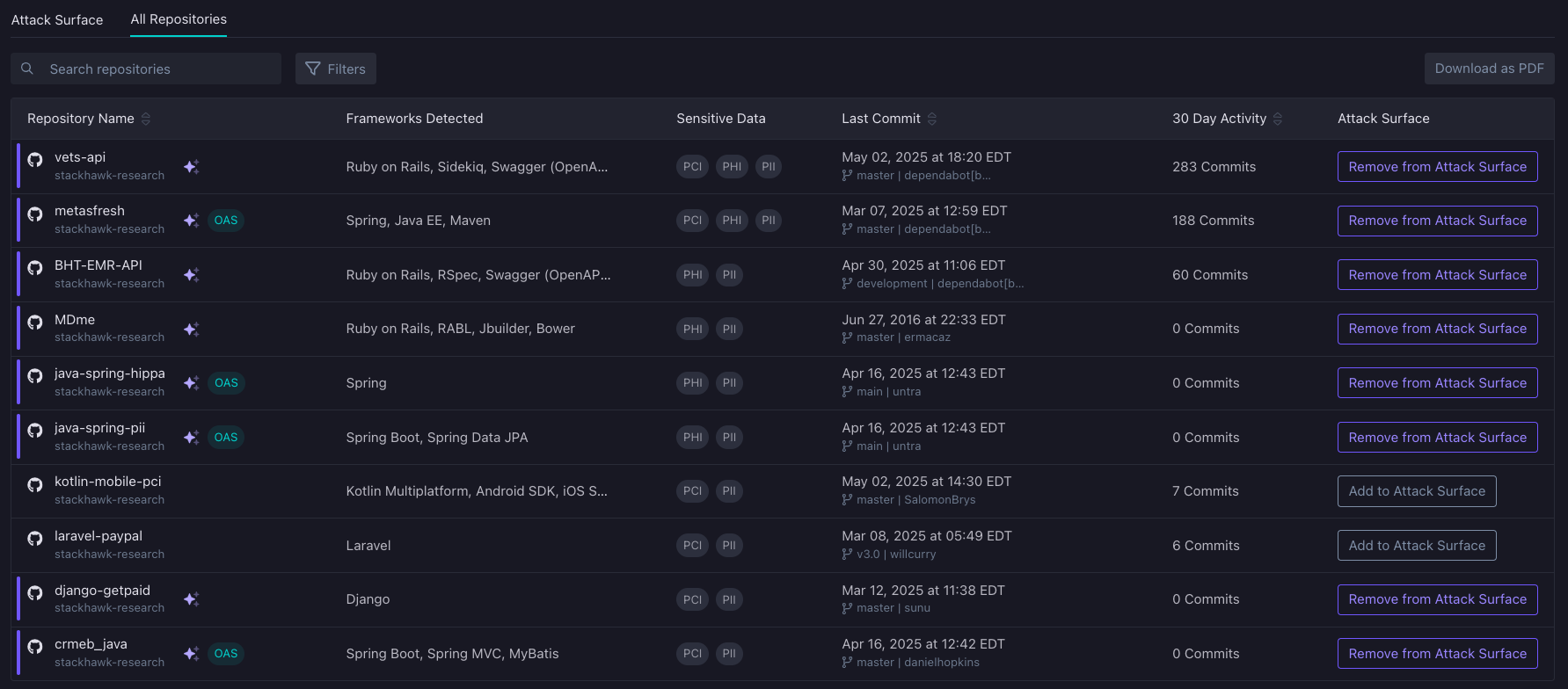
All Repositories
The All Repositories view shows all of the repositories you have given StackHawk access to with the ability to add to or remove from the Attack Surface. In this view you can see the name of the repository, its status within StackHawk, the frameworks detected by HawkAI, last commit information and recent commit activity.
StackHawk Application
StackHawk supports multiple configurations to connect your repositories to StackHawk applications, tailored to different organizational needs:
- Single Repo - For organizations that store their apps and API code in separate repositories, you can quickly connect each repository to its corresponding StackHawk application.
- Mono Repo - If your organization uses a monorepo structure (multiple apps and APIs in one codebase), you can seamlessly connect one repository to multiple StackHawk applications.
- Microservice Repos - For organizations with numerous microservices that integrate into a single StackHawk application, you can easily connect several repositories to a single StackHawk application.
Frameworks Detected
HawkAI enhances visibility by detecting and displaying the frameworks present in each repository. This detailed view helps you understand the type of API or Web Application and streamline the process of getting it under test with StackHawk.
Last Commit
Stay synchronized with new code deployments by tracking the last commit details, including the branch name and the developer who committed the code. This feature allows you to invite developers to the StackHawk platform quickly, ensuring they can promptly address and fix vulnerabilities.
30 Day Activity
Understanding the frequency of code commits to a repository helps prioritize which repositories to test first. It also aids in determining the optimal testing frequency to ensure that no code reaches production without being secured by StackHawk.
OpenAPI Specification Generation
See OpenAPI Specification Generation
Disabling HawkAI
We recognize that some organizations have strict policies and procedures regarding the use of large language models (LLMs) and the sharing of data with third-party services. To accommodate these requirements, StackHawk provides an easy way to disable all AI processing. You can disable HawkAI by navigating to Settings -> Org Settings -> HawkAI under General AI Usage. Disabling this ensures that no AI processing will occur, aligning with your organization’s compliance and data sharing policies.
For more information on how StackHawk handles and protects your data, please read our blog post: How We Built HawkAI to Protect Your Data.