Scan Policy Management
This feature is available on the StackHawk Enterprise plan.
When you run a security test with HawkScan, the scanner uses a default selection of plugins that correspond to common vulnerability tests. This set of plugins is a scan policy. StackHawk offers multiple scan policies, that include different plugins depending on the type of application you are testing. Which scan policy runs during a scan on your application is determined by the configuration in your stackhawk.yml.
Scan policies and the plugins/tests that run during scans can now be explicitly configured for each application in the StackHawk Platform.
Scan Policy Selection
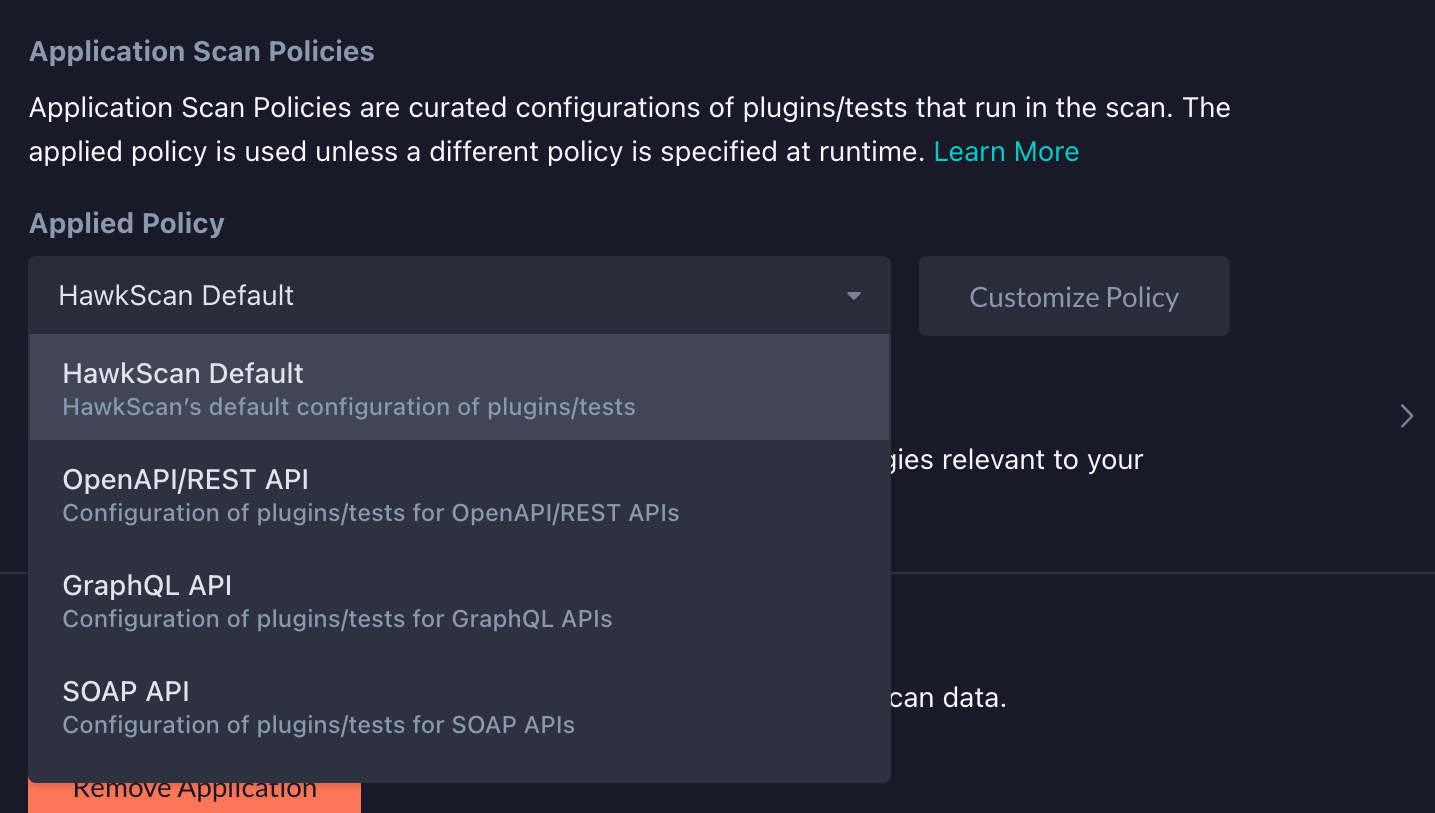
To select which policy runs during a scan:
- Go to the Applications Page.
- Click the application name to go to the Settings page.
- Under Application Scan Policies, use the Applied Policy dropdown menu to select a scan policy that will run during scans of this application.
Customize Scan Policy
An application scan policy can be customized to have more fine-grained control over which plugins/tests run as part of the policy. You may want to add or remove plugins/tests from a policy to decrease scan time or focus a scan on certain vulnerabilities.
NOTE: Cross Site Scripting (DOM Based) (plugin ID 40026) requires use of the ajax spider.
To customize an application scan policy:
- Select an application scan policy from the Applied Policy dropdown menu and click Customize Policy.
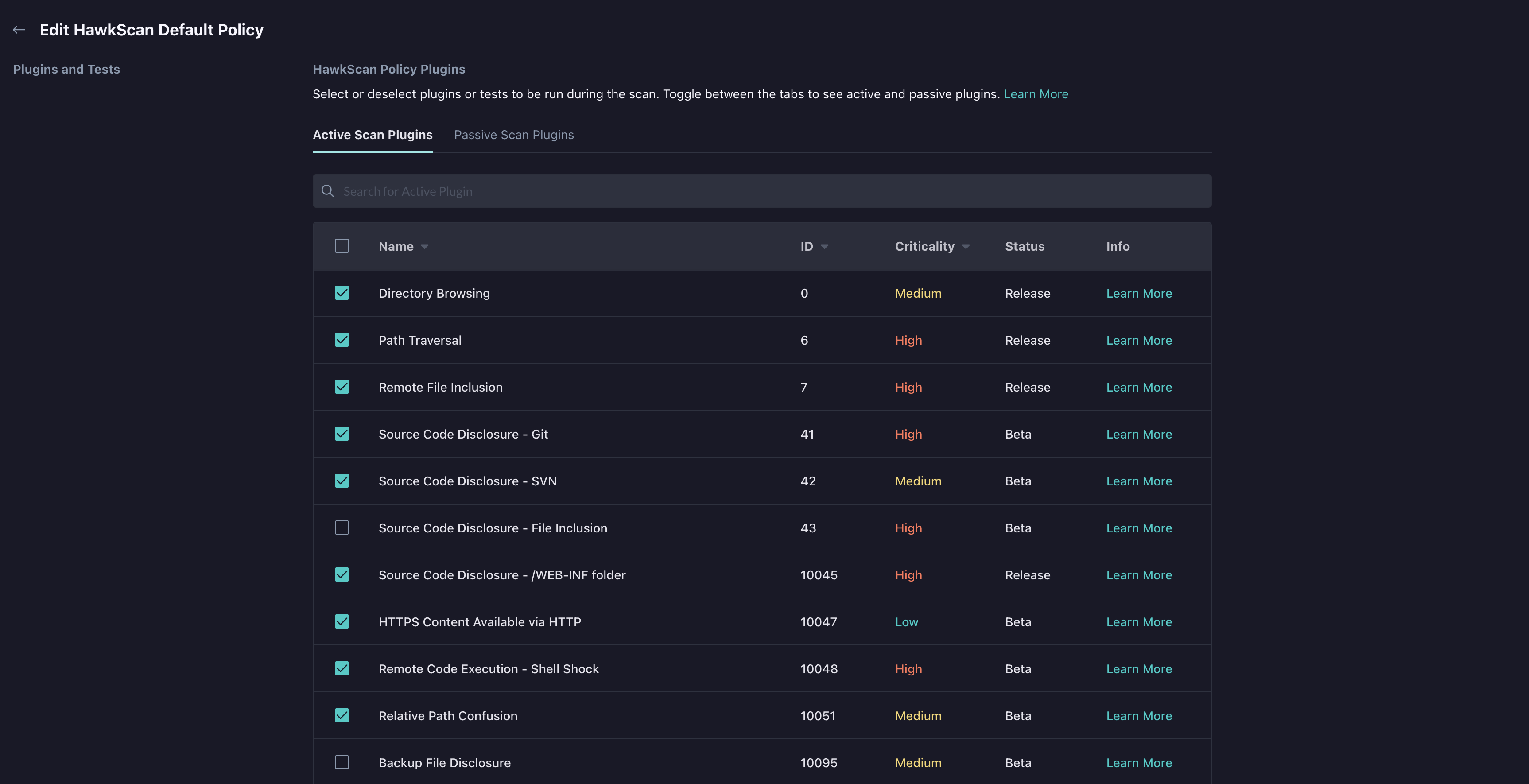
- On the Policy Management page, click the checkboxes to enable or disable the plugins/tests you want to include or remove from your application scan policy.
- Your updates take immediate effect and a customized label is applied to the application scan policy.
The list of plugins on the Policy Management page contains two tabs for each plugin/test type. Active scan plugins attempt to exploit vulnerabilities while passive scan plugins make normal requests to an application and analyze the responses.
You can use the search bar above the plugins list to search for plugins by name, ID, criticality and release status.
Clicking an unchecked checkbox will enable the plugin/test while clicking a checked checkbox will disable the plugin/test.
After you customize the applied application scan policy, if you apply a different application scan policy, you will lose your customized configuration.
Permissions
Selecting and customizing scan policies from an application’s Settings page are only enabled for owners and admins whose organization is on an Enterprise Plan. Organization members will still be able to run scans against applications with scan policies that have been selected or customized from this page.
Prioritization
In addition to changing the applied policy and customizing a scan policy in Settings, there are two ways that scan policies may be applied in the stackhawk.yml configuration file.
- Configuring the
hawk.scan.policyNameparameter. Read more - Configuring the
app.openApiConf,app.graphqlConforapp.soapConfparameters. Using one of these parameters will normally cause HawkScan to automatically select a scan policy that is optimized for OpenAPI/REST, GraphQL or SOAP APIs. Read more about configurations for OpenAPI/REST, GraphQL or SOAP APIs.
The following list is the order of priority for the various methods of applying scan policies:
- Scan policy set with
hawk.scan.policyNamein the StackHawk YAML configuration file,stackhawk.yml. - Customized applied policy on the application’s Settings page in the StackHawk Platform.
- Applied policy, other than HawkScan Default, in the application’s Settings page in the StackHawk Platform.
- OpenAPI/REST, GraphQL, or SOAP-optimized scan policies when:
- One of the
app.openApiConf,app.graphqlConf, orapp.soapConfparameters are configured in the StackHawk YAML configuration file,stackhawk.yml. - The applied policy is HawkScan Default (or was never previously configured) on the application’s Settings page in the StackHawk Platform.
- One of the
- HawkScan Default scan policy when the applied policy is HawkScan Default (or was never previously configured) on the application’s Settings page in the StackHawk Platform.
Best practice is to use one of these configurations at a time for each application.
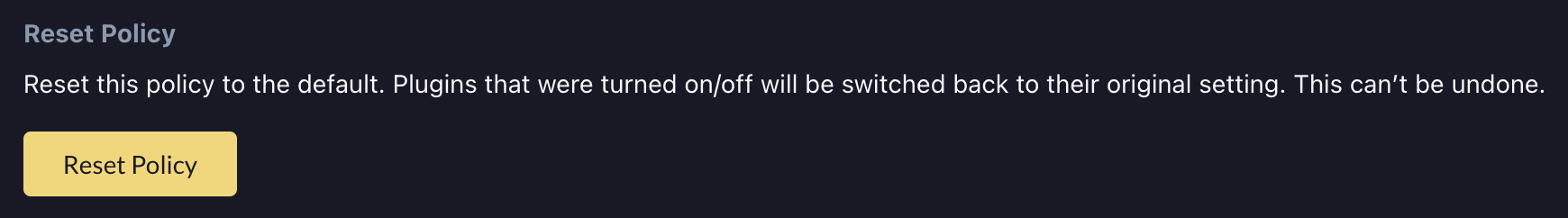
Reset Scan Policy
To reset a scan policy back to its original enabled/disabled plugin selection, use the Reset Policy button on the Policy Management page.
Video Tutorial
Check out our video tutorial on Policy Management:
